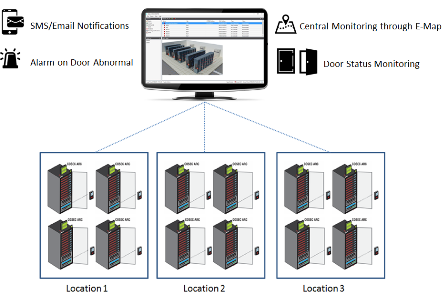
Solution:
Access Control for Data Centers
About Solution:
Data Centers is a challenging domain, the success of which depends on security of client data. Most Data Centers store data for more than one organization. It is very crucial for Data Centers to prevent any unauthorized access of data. Matrix offers a solution whereby data racks are secured biometrically, with records of every access along with its duration. Only authorized person can access specific racks for the stipulated time using biometric verification.
How it works?
The solution is available in two forms, the process of which is listed below:
Solution 1: Time based Rack Access with Single Biometric Device
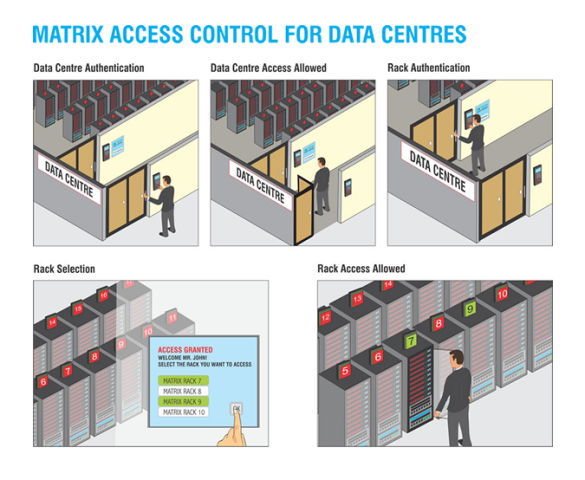 Data Centre Authentication: User shows biometric credentials to access the Data Centre.
Data Centre Authentication: User shows biometric credentials to access the Data Centre.
Data Centre Access allowed: Once user is allowed Access, he/she will move towards rack access authentication.
Rack Authentication: User will click on the screen and authenticate his/her identity through a biometric device placed alongside the screen.
Rack Selection: Once user completes the authentication process for gaining access to respective racks, he will be able to select the racks to be accessed from a list of accessible racks.
Rack Access Allowed: Finally, the user will perform his assigned task within the defined time period.
Solution Description:
The features mentioned below enhance security of Data Centers:
- Centralized Biometric Authentication:
Biometrics provides high-end security over RFID, and hence, integrating biometrics with Access Control solution fetches complete security for Data Centers. Usually, an employee is required to punch twice in order to access the data rack of his/her organization.
- First Punch: A biometric device will be installed at the entrance of the Data Centre. A user will punch on the device and accordingly he/she will be granted/denied access. This authentication ensures that an authorized user is trying to access the data center.
- Second Punch: Once user is granted access, he/she will punch again at the device installed near the screen in order to access the respective racks. Once user punches, the screen will display the list of racks that he/she is allowed to access. For example – when ‘X’ employee of ‘ABC Organization’ punches second time, the screen will display a list of ABC Organization racks that are allotted to him. The user then needs to select the racks that he wants to access accordingly, he/she will be granted access.
- Pre-defined Rack Access:
Every company has designated racks allotted to them. Admin can define the racks company-wise, which means whenever a user makes his second punch – a list with racks allotted to his/her respective company will be displayed on the screen.
This feature acts as a USP for Data Centers as they can ensure that a rack of company “X” will not be accessible to or misused by an employee of company “Y”
- Rack Accessible for a Defined Time Period:
Every rack that is allocated to a company can only be accessed for a definite period of time. Admin can set the duration and accordingly users can access their respective racks for the stipulated time period.
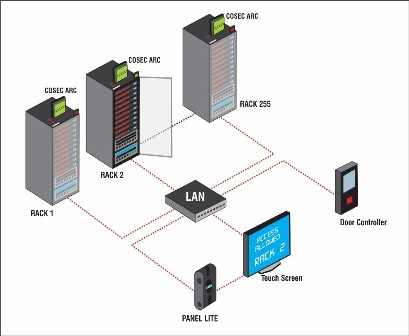
Connectivity Diagram:
 Solution 2: User Based Rack Access with Multiple Biometric Device
Solution 2: User Based Rack Access with Multiple Biometric Device
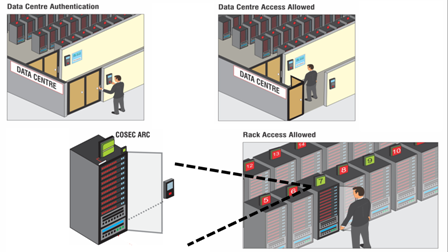 Data Centre Authentication: User shows biometric credentials to access the Data Centre.
Data Centre Authentication: User shows biometric credentials to access the Data Centre.
Data Centre Access allowed: Once user is allowed access, he/she will move towards rack access authentication.
Rack Authentication: User will show biometric credentials to access the rack.
- Solution Description:
The features mentioned below enhance security of data centers:
- Centralized Biometric Authentication:
Biometrics provides high-end security over RFID, and hence, integrating biometrics with Access Control solution fetches complete security for Data Centers. Usually, an employee needs to punch twice in order to access the data rack of his/her organization.
First Punch with Two Level Authentication: A biometric device will be installed at the entrance of the Data Centre. User will show Card or Enter the Pin Code then Biometric Credential on the device, and accordingly he/she will be granted/denied access. This authentication ensures that an authorized user is trying to access the Data Centre. Two level authentication improves the security level.
- Second Punch: User will move to the rack and show his/her biometric credential on the device installed at the rack. If the User is authenticated a user will be allowed to work in the rack for a pre-defined period of time and once finished, the device will close the door automatically.
- Pre-defined Rack Access:
Every company has designated racks allotted to them. Admin can define the racks company-wise, which means whenever a user makes his second punch – a list of ABC Organization racks that are allotted to him will be displayed on the screen.
This feature acts as USP for Data Centers as they can ensure that a rack of company “X” will not be accessible to or misused by employee of company “Y”
- Integration with Video Surveillance:
Matrix Access Control solution for Data Centers can be integrated with the Video Surveillance solution. Hence, when a user tries to access the Data Centre through the biometric device, an image gets captured. In case of unauthorized access, having an image can prove helpful for Data Centers.
- Rack Accessible for a Defined Time Period:
Every rack that is allocated to a company can only be accessed for a definite period of time. Admin can set the duration, and accordingly the rack will be accessible for the pre-defined time period.
Connectivity Diagram:
‘Data Rack’ Management:
Data Centers have data of more than one organization stored in a single location. Managing the data racks is a cumbersome process for Data Centers. Through this solution, Data Centers can manage each and every company’s rack virtually along with enhancing the security.
Reports:
The solution provides reports for:
- ‘Which’ Rack is Accessed by ‘Whom’, ‘When’ for ‘What’ Time Duration
- Records Related to Rack Accessibility, Time Duration, etc.
- Alarm for a Rack Held Open for too Long, Access Denied Events,
Benefits:
From Data Centre point of view:
- Easy Maintenance of Diverse Data
- Accurate Record of Access Allowed/Denied in the Software
- No Manual Security Required
- Easy Data Rack Management of Various Companies in a Single Location
From Companies Securing Data at Data Centers:
- Complete Security of Company Data
- Accurate Records of Who Accessed Data at What Time
Target User Profile:
- Data Centers
- Server based Companies