Development platform for secure IoT designs
 With the increasing market penetration of new solutions for the IoT (Internet of Things) and the highly dynamic markets, for many companies checking and testing their products alone before they leave production no longer suffices. On the contrary, the products have to be monitored and maintained in the field over their entire lifecycle as well as performing any updates/upgrades required. Against this background, ongoing and/or remote services are offered for the support and maintenance of installed equipment. This also entails having to equip numerous electronic products with corresponding sensors and measuring instruments in order to allow developers to test and/or modify a system or machine remotely – often as a means of predictive maintenance. For this purpose, secure access via VPN (virtual private network) is required for the remote diagnosis in order to avoid time and cost-intensive on-site visits. The scope of applications is correspondingly broad and ranges from heating maintenance to software updates for a robotic system through to ‘smart farming’.
With the increasing market penetration of new solutions for the IoT (Internet of Things) and the highly dynamic markets, for many companies checking and testing their products alone before they leave production no longer suffices. On the contrary, the products have to be monitored and maintained in the field over their entire lifecycle as well as performing any updates/upgrades required. Against this background, ongoing and/or remote services are offered for the support and maintenance of installed equipment. This also entails having to equip numerous electronic products with corresponding sensors and measuring instruments in order to allow developers to test and/or modify a system or machine remotely – often as a means of predictive maintenance. For this purpose, secure access via VPN (virtual private network) is required for the remote diagnosis in order to avoid time and cost-intensive on-site visits. The scope of applications is correspondingly broad and ranges from heating maintenance to software updates for a robotic system through to ‘smart farming’.
The components used in the complex supply chains, as well as in remote development and maintenance for the IoT, do however present new opportunities for attackers. From the theft of sensitive data and intellectual property (IP) through to the manipulation of an entire system platform – the challenges in terms of security have to be addressed. Many IoT companies, however, are lacking the necessary security expertise.
The Infineon Security Partner Network (ISPN) was set up in 2015 in order to address original equipment manufacturers (OEM) and their end customers within the extensive IoT ecosystem with easy to implement, hardware-based security solutions. The members of the ISPN offer manufacturers of connected devices and providers of IoT services precisely tailored security solutions. This network highlights which security requirements exist within the context of the respective application and offers support with the implementation of security solutions. In doing so, the partners use hardware-based security as a trust anchor in connected devices.
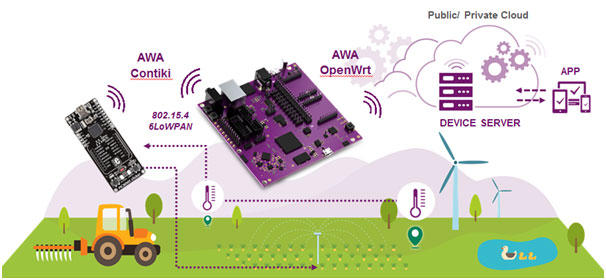
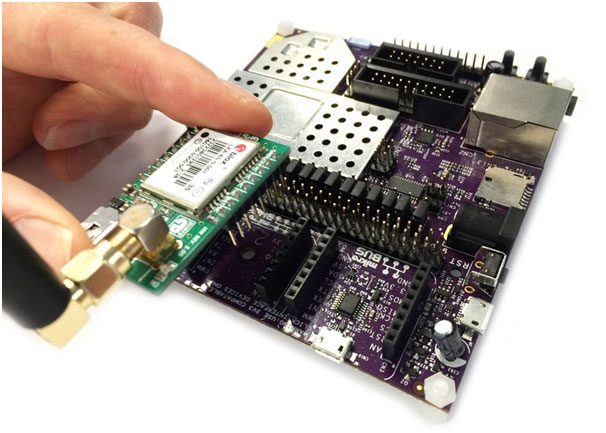
One such ISPN member is Imagination Technologies, who have developed the Creator Ci40 and the Ci40 IoT-in-a-box kit (Fig. 1). This development tool allows developers to deal with the security implementation for their IoT design at an early stage. The MIPS-based Creator Ci40 platform uses the Infineon OPTIGA™ TPM (Trusted Platform Module) security controller (Fig. 2) for storing the keys and certificates.

Different worlds
Despite security indisputably being a key factor for every professional IoT solution and meriting corresponding attention, the reality often looks quite different. In many cases, developers do not have the tools or resources in order to implement a robust security solution. If, however, the security solution is only implemented at the end of the design cycle, the outcome is mostly unsatisfactory. Unintentional attack surfaces are often created. Numerous embedded development boards for IoT applications are already available on the market, mostly however without corresponding security functions. What is more, a scalable open source IoT framework, which ensures a reliable and secure connection with the cloud, is frequently difficult to find. The Creator Ci40 provides an open source board as an IoT hub with software support, which uses the OPTIGA TPM for storing the keys, a verified boot process and other security functions.
Security throughout the entire product cycle
Security IoT solutions consist – as stated above – not only of one device or product, which is shipped and subsequently left to itself. Every IoT development platform must therefore provide a flexible, scalable and secure framework, which can be used throughout the entire product cycle.
Thanks to its open source character, developers can use the Creator LWM2M & IPSO IoT framework to control, maintain and manage their designs day and night. As such, the key criteria for a professional IoT solution are satisfied:
– cost-efficient scaling
– robust and secure platform
– a framework that can work with old and new components from different manufacturers
– an open source framework that is based on open standards, which has no proprietary lock-ins, making it future-proof
Targeted design support
For an efficient implementation of secure IoT designs, the Creator team has developed a number of design examples and made these available on GitHub. What is more, a verified boot implementation, helpful TPM tool packages and the TrouSerS package ported onto the Creator Ci40 platform are available. Specific examples of the operation of the TPM as the Universal Boot Loader (U-Boot) and with Linux on the Creator Ci40 platform can also be found on GitHub:
https://github.com/CreatorDev/u-boot
https://github.com/openwrt/openwrt/pull/131
https://github.com/CreatorDev/Ci40-platform-feed/pull/69
Summary
The Creator Ci40 IoT development platform acts as the IoT hub, which gathers the data from multiple sensors and processes of the application either locally or via the cloud. The Linux-compatible platform features multiple wireless interfaces and with the OPTIGA TPM also incorporates standardised and certified hardware security. The development board provides a quick and easy means of implementing security solutions. At the same time, it is possible to use the OPTIGA TPM, for example, to safeguard the secure boot process. The TPM also features roll-back protection for the firmware, i.e. it helps to prevent attackers from replacing newer software with older or malicious software. Further information on the Creator Ci40 IoT kit is available at http://www.creatordev.io. The kits are available from the distributors RS Components and Mouser.

Everything on board
The Ci40 platform offers everything for the rapid development of a secure IoT solution. Using sensors and actuators on edge boards and an IoT hub allows the corresponding devices to be securely connected and managed. The scope of delivery also includes a scalable object device management platform. The open source framework LWM2M + IPSO is based on the Open Mobile Alliance.
The kit features an IoT hub on the basis of a Linux-compatible dual-core MIPS-CPU (multi-threaded) with three wireless interfaces on the Ci40 mainboard (802.15.4 6LoWPAN, 802.11.AC Wi-Fi and Bluetooth) and possible extensions (e.g. via USB). Three (MikroElektronika) click boards and two further battery-powered 6LoWPAN clicker boardsallow numerous sensors and actuators to be connected. The MIPS-CPU with 550 MHz offers sufficient power for processing the sensor data.
A TinyDTLS (datagram transport layer security) is responsible for encrypting the sensor data from the ‘edge device’, while the OPTIGA TPM stores the keys in the IoT hub and ensures the secure connection from the sensor side to the cloud and a secure boot process.
OPTIGA TPM for secure IoT designs
The OPTIGA TPM chips (Trusted Platform Module) cover an extensive and standardised range of security functions. These special security chips are based on the international, open standard of the Trusted Computing Group (TCG). After TPM chips having successfully proven themselves for years in computer applications, this technology is now also finding its way on account of the increased security requirements into connected industrial systems such as IoT and Industry 4.0. TPMs acts as data safes and support authentication and encryption. Keys and/or certificates stored in the TPM do not need to leave the security chip, thus protecting them effectively against unauthorised use.
At the same time, TPM chips perform multiple functions:
– Comparable with an electronic proof of identity, they securely identify the individual system components. Persons and devices acquire access to the network if they are authorised.
– On device level, they provide the basis for detecting manipulation or attacks on components or the device itself. This allows both logical and physical attacks to be detected and corresponding, predefined measures initiated.
– As data safes, they safeguard confidential information, which is necessary for a secure communication channel for encryption.






