Simon Holt, Mouser Electronics
Networks used to be about connecting computers together, but the Internet of Things (IoT) has changed all that, creating a web of devices on an unprecedented scale. The IoT already comprises billions of devices, and that number is growing daily in places such as homes, offices, factories and public buildings. The IoT already carries significant amounts of data, much of which can be considered sensitive in nature, and as the IoT expands to encompass more critical functions, this too will increase.
The IoT poses many challenges for designers; one of the most significant is its sheer scale, which gives billions of potential access points for hackers, requiring engineers to provide protection. This technical article looks at how engineers are deploying hardware and strategies to keep IoT data safe in an increasingly hostile world, while continuing to meet the cost and power constraints of the IoT.
The IoT promises a bright future for a connected world that will benefit all citizens, delivering benefits such as advanced monitoring, automated homes and workplaces, smart factories and more, culminating in a smart world. Comprising billions of simple devices that are connected, the value of the IoT lies in the ability for machines to communicate directly with machines – yet this is also an “Achilles heel” for the future.
Every one of these IoT nodes forms part of a huge attack surface that can be exploited by malicious individuals or organizations. Once security is breached, the connectivity renders the whole network liable to attack, which can include denial of service (DoS) attacks that bring the network down, or the theft of sensitive data and intellectual property.
While there are many considerations surrounding IoT security, the primary concern is with the “brain” of the system – the microcontroller (MCU), as well as the software that runs on each MCU. Modern MCUs are more secure than their predecessors and often integrate cryptographic/authentication engines, built-in security blocks, key management functions and tamper detection/prevention features. Wireline and wireless communication protocols are moving toward requiring encryption/decryption so that data entering and leaving the node is fully protected.
The boot-up phase of the MCU is critical, as it is here that code provided by a malicious source could be introduced to the system. Secure boot routines rely heavily on a “root of trust” being established via strong certification and authentication mechanisms that will ensure the validity of any software before it is executed. The mechanisms will detect any alteration to the software and prevent it from being executed. One method of securing the software against tampering is to store it in non-volatile memory that has strong inbuilt security features, thereby preventing replacement or modification.
Hash Codes and Keys
Hash codes are similar to checksums in that they are generated by applying a mathematical algorithm to a digital asset, such as a piece of software code. These provide security, as each digital asset has its own unique associated code that can be validated at any time by regenerating the hash code. The regenerated hash code is then compared with the original, and any difference indicates that the digital asset has been changed in some way.
However, hash codes generally require a fairly significant amount of computing power as well as electrical energy to execute. This provides challenges in the IoT environment where MCUs are generally low performance, and energy reserves (usually in a battery) are small.
Another means of providing security is through the use of keys. This is generally known as cryptography, and there are two main approaches/types. Symmetric encryption is simple; the sender and recipient have identical keys and use these for encryption/decryption. The weakness is that if the key is intercepted or otherwise discovered, then all data can be decrypted and the encryption is useless.
The asymmetric key approach relies on two keys: a private key (which is kept secret), and a public key (which is shared). When the keys are generated, there is no difference in their status and either can be public or private. The way in which they are used and stored after generation is what defines each role.
Again, an algorithm is used to generate the two keys, which are different but complementary. Data encrypted by one key is decrypted by the other, although having access to the public key does not allow the private key to be decrypted. The public key can be shared widely (some have even been posted on the Internet to demonstrate the concept) without undermining security.
The main caveat is that any data encrypted by the public key cannot be trusted, as the key could be widely available. However, anything encrypted via the private key can be safely decrypted by the public key. This (asymmetric) approach is much stronger that the symmetric approach, but it does require even more computational power.
Removing the Burden on the MCU
Almost all IoT nodes have constraints on the available power as well as the manufacturing cost, meaning that relatively low-end MCUs are specified to meet the day-to-day operational needs of the node, which are generally low. In order to meet the computing needs for security without over-specifying the MCU, co-processor ICs are increasingly being used as a very effective solution.
Infineon’s OPTIGA family of trusted platform modules (TPMs) is a comprehensive range of devices that can perform asymmetric encryption on their inbuilt hardware accelerators. These accelerators are able to support elliptic curve cryptography (ECC) and Rivest Shamir Adleman (RSA) algorithms and contain the algorithms necessary to generate SHA-1 and SHA-256 hash codes. By using OPTIGA co-processors, there is no security load on the MCU, as all encryption/decryption is delegated to the co-processor. As a result, high levels of security are created without loading the MCU, or requiring a more powerful MCU to be specified.
 Figure 1: The Infineon OPTIGA TPMs.
Figure 1: The Infineon OPTIGA TPMs.
Creating a root of trust is relatively easy with Maxim Integrated’s DS28C36 secure authentication chip. This device can be used in conjunction with an MCU and external non-volatile memory (NVRAM), enabling simple low-cost hardware to perform complex operations such as secure boot or firmware-over-the-air (FOTA) updates. The DS28C36 uses a combination of public and private keys as well as SHA-256 hash codes to ensure software is authentic before the MCU is permitted to execute it.
In practice, the equipment manufacturer of a node that uses the DS28C36 would generate the public and private keys within a secure manufacturing site and the private key would be securely retained there so it cannot be intercepted. This key is used to encrypt the firmware on the node, and the public key is incorporated into the node before it is shipped to the end user.
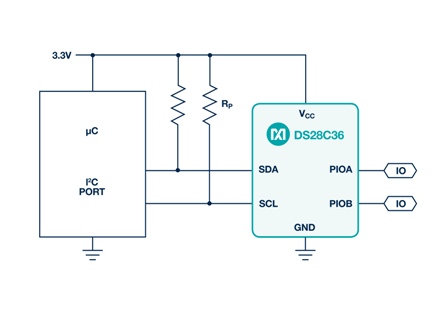 Figure 2: Typical application circuit from a Maxim DS28C36 authentication IC.
Figure 2: Typical application circuit from a Maxim DS28C36 authentication IC.
When the node has been deployed, each time it powers up the encrypted firmware is loaded by the MCU but is not executed. The onboard boot manager (within the MCU) obtains the hash code and sends it to the DS28C36. which generates a fresh hash code based on the status of the firmware that has loaded. The hash code is compared to the one that was generated in the secure manufacturing environment (using the private key) and, if they match, the MCU is allowed to execute the firmware.
 Figure 3: Microchip’s ATECC608A.
Figure 3: Microchip’s ATECC608A.
Another advanced cryptographic co-processor is Microchip’s ATECC608A, which has the capability to store as many as 16 separate keys. The device supports asymmetric signing, verification and key agreement via the elliptic curve digital signature algorithm (ECDSA), elliptic curve Diffie-Hellman (ECDH) and NIST standard P256 elliptic curves. Additionally, it includes symmetric algorithm hardware accelerators for SHA-256 hash codes and AES-128 compliant encryption/decryption, as well as secure boot.
Microchip’s solution is designed to address every aspect of key operations, including private key generation, ECDH key agreement, ECDSA signature generation and ECDSA public key signature verification. It is also able to generate random private keys while permanently retaining the private key for security. The corresponding public key can be generated simultaneously, or at any point in the future.
 As the ATECC608A can run asymmetric cryptographic functions much faster (1000x faster) than a standard MCU/software combination, it facilitates very high-performance security in IoT applications.
As the ATECC608A can run asymmetric cryptographic functions much faster (1000x faster) than a standard MCU/software combination, it facilitates very high-performance security in IoT applications.
Clearly, security is a huge topic for the IoT, and security needs to be strong to protect the integrity of this network that covers the planet. Using MCUs is self-defeating, as it will raise cost and power consumption, either of which would negate many of the benefits of the IoT. For this reason, dedicated security co-processors are becoming an extremely popular method of ensuring high levels of security in IoT nodes.






