Prashant Pandey, Senior Staff Engineer, STMicroelectronics and Himalya Bansal, Business Development Manager, LDRA India

We have witnessed over one trillion semiconductors’ sales for the first time [1] in the last decade. The semiconductor industry has also seen the growth of customised application specific integrated circuits (ASICs) & field programmable gate arrays (FPGAs).Internet of Things (IoT) is one of the important contributors to this growth, where the forecast[2] is of having 41.6 billion connected devices generating 79.4 zettabytes (ZB) of data in 2025.
Due to its pervasive nature and relatively weak security, IoT devices present an extremely valuable target for the attackers, and hence there is a strong need to protect these devices. Contrary to popular belief that cybersecurity refers to software security only, to design an overall secure system, software security alone is not sufficient. There are many aspects of security that need to be enforced at the hardware level. In a secure design, each module involved must be secured, but it cannot be done in isolation. There is a need for a trusted security handshake between different modules. Insecure internal interfaces could lead to system-level exploits such as Bleeding Bit[3], where malicious advertising packets (BLE broadcast messages) overflow the firmware stack, allowing an attacker to gain control of the chip.
As segments like automobile, medical and infrastructure start using IoT more and more, security breaches could have serious consequences, such as heavy financial damage, loss of human life, and even threat to national security.
Counterfeit chips – A concern for national security
As per the “Defense Industry Base Assessment: Counterfeit Electronics” report[4], 55% of integrated circuit (IC) manufacturers surveyed reported that they had encountered counterfeit versions of their products. To address this issue, SIA (Semiconductor Industry Association) has created an Anti-Counterfeiting Task Force. The team submitted their comments[5]to GSA in2018 where reference were made to suspect counterfeit semiconductor components in a range of military systems such as THAAD missile, military aircraft helicopters, military transport planes, and a military plane with antisubmarine and anti-surface warfare capabilities. Such Counterfeit chips may carry viruses or malware that can weaken national security.
Reference can be made to standards like SAE AS5553C titled “Counterfeit Electrical, Electronic, and Electromechanical (EEE) Parts; Avoidance, Detection, Mitigation, and Disposition” and the worldwide programs like SHIELD (Supply Chain Hardware Integrity for Electronics Defense) by US DARPA (Defense Advanced Research Projects Agency).
Architecture and design for security
It focuses on security by design and recommends splitting the system into various intercommunicating subsystems with appropriate privilege set. One way to achieve this is to adopt MILS architecture (multiple independent levels of safety/security) where secure zones are created. It is based on principles of separation and controlled information flow. Initially, this architecture was for defence, but it is widely adopted by other industries involving high-integrity systems.
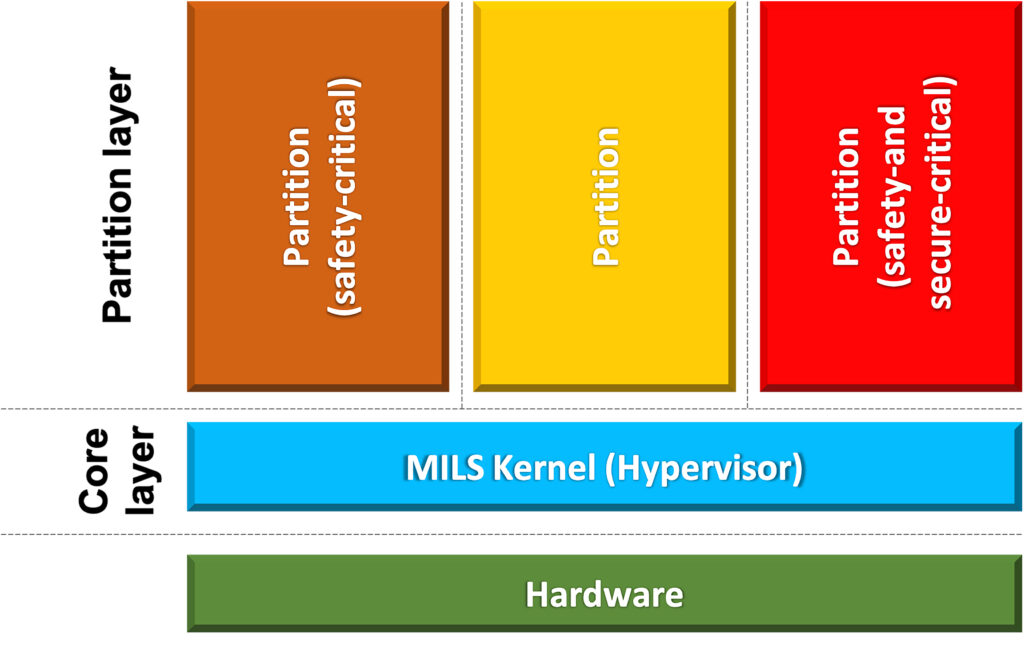
Practice defence in depth: IoT security needs to be layered to make it extremely difficult for the attackers to gain access to important data. For example, consider “logic locking”, a method to prevent IP piracy against an untrusted entity in the supply chain by embedding key-gates in the design. A logic locking may become vulnerable if the key values are exposed; hence, a team of researchers at Cornell University[6] proposed a defence-in-depth approach (as per below table) to protect the locking key according to the potential threat model.
| Layer 1 | Hardware Assurance |
| Layer 2 | Defence against reverse engineering |
| Layer 3 | Defence against contactless probing |
| Layer 4 | Defence against contact-based probing |
| Layer 5 | Defence for design-for-test |
| Layer 6 | Defence for logic obfuscation techniques |
Hardware Roots of Trust (HRoT)
A HRoT builds core security mechanisms into the actual hardware, and it enables secure performs functions such as secure boot, secure key/signature storage, memory protection, secure firmware and software updates, access control policies for System-on-Chip (SoC) peripherals, Trusted Execution Environments (TEEs), etc.
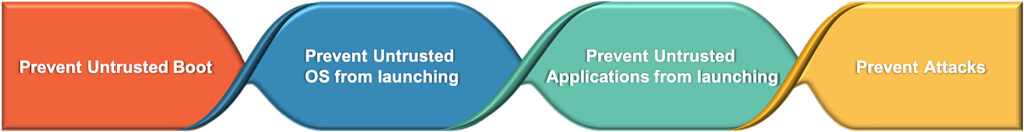
Secure gateways for Secure communications
In IoT networks, gateways act as a hub point in the network where all data is collected. Gateways are subject to various malicious threats like spoofing, eavesdropping, man-in-the-middle (MITM) attacks, data snooping, jamming, etc. Layered security across all 7 layers of OSI model is needed to address these risks. Apart from securing the communication interfaces, the gateways themselves must be secured too. One way to achieve this is to use trusted platform modules (TPM) based on Trusted Execution Environments (TEE) function of HRoT and provide secure storage of credentials and protected execution of cryptographic operations.
Secure Authentication
Consider the example of IoT gateways with 3 types of interfaces, i.e., to user’s mobile devices, local IoT devices, and the cloud (external world). IoT devices connect to the external world through gateways, and the devices & gateways need to establish their strong identity. This identity is used for secure authentication to ensure that an external world connection is established with a legitimate device and not with a fraudulent source. Nowadays, dedicated security chips are available to securely store symmetric and asymmetric cryptographic keys while providing robust protection against various cryptographic attacks. While providing a unique identity to the device, these chips provide a feature to encrypt data and authenticate devices, data, and commands, as required in IEC 62443,thus significantly reducing \the chances of unauthorised access. An example includes STMicroelectronics STSAFE-A110 secure elementIC[7].
Security lifecycle management: The IoT security must cover the entire lifecycle of thedevices and include all phases of design, manufacturing, installation, use and decommissioning. For example, consider a scenario if a device is thrown away in waste due to missing e-waste policies. The scrapped device is reused to connect to a secure service without authorisation. This can be addressed via secure device decommissioning, where the reference can be made toIPC-1782 standard titled “Standard for Manufacturing and Supply Chain Traceability of Electronic Products”. In the case of automotive, it is referenced in SAE J3061 Clause 5.7, and there is a NIST special publication 800-88 titled “Guidelines for Media Sanitization”.
The big lesson learnt from Solar Winds supply chain attack is that the software even from well-trusted sources can be compromised. Thus, there is a need to address security throughout the lifecycleand also throughout the supply chain. Here are some general principles for securing IoT Devices from Australia &the UK government’s IoT Code of practice derived from ETSI TS 103 645[8]
1. No duplicate, default or weak passwords: All network devices should ship with a strong and unique default password. The user should be instructed to change the password on the first use of the device. The device must ensure that the user sets a strong password.
2. Implement a vulnerability disclosure policy: As the new vulnerabilities are being discovered in products every day. It’s important that a mechanism is in place to allow security researchers to inform the manufacturer about the vulnerability. The manufacturer should also transparently disclose the vulnerability when patch is available so that the users can apply the patch.
3. Keep software securely updated: The manufacturer should provide security patches throughout the product lifecycle. There should be checks to ensure that firmware is validated before flashing, and a downgrade to a less secure older version should not be allowed.
4. Securely store credentials: Credentials should be stored in a secure manner e.g. encrypted and preferably in a secure element.
5. Ensure that personal data is protected: Privacy is not only a desirable attribute of a product, it is mandated by strong laws like GDPR. However, it requires effort to secure data using encryption mechanisms and all parties’ thorough involvement to follow best practices while handling user data.
6. Minimise attack surface: Devices should provide the least privilege to processes and users to do their job. Also, any hardware interfaces like JTAG, serial ports or software interface like ports not required for product operation should be protected.
7. Ensure communication security: Industry-standard encryption algorithms should be used for the transmission and storage of data.
8. Ensure software integrity: Feature like secure boot should be utilised to ensure that any unrecognised piece of software should not be allowed to run at any point of operation of the device.
9. Make systems resilient to outages: Redundancies and backups should be incorporated in various IoT subsystems to ensure that the system does not become non-functional if a subsystem fails.
10. Monitor System Telemetry data: Telemetry data indicate the device’s health and help identify a compromised device in the network using the device’s behaviour.
11. Make it easy for the customer to delete personal data: This is especially useful when there is a need to transfer the ownership of the device, or the device needs to be disposed of. There should be easy to use options in the device that can export and delete all of the user’s data stored on the device.
12. Make installation and maintenance of the devices easy: Many security vulnerabilities ensue from the incorrect installation of devices. Having user documentation and easy to follow instructions for life cycle management if the devices can better secure these devices.
13. Validate input data: Processing unvalidated user input can give rise to a huge class of attacks called an injection attack. Examples of such attacks are code injection, SQL injection etc. User input must be sanitised to ensure that it does not contain any executable components and the parameters provided are within range.
Examples of Cyber-attacks
Hardware Attacks: Hardware attacks often happens due to undetected vulnerabilities at the semiconductor design process or via firmware. These attacks can occur at various stages of the product lifecycle and could result in chip malfunction, denial of service or sensitive information breach. There is a possibility that a well-designed hardware vulnerability could go undetected due to the complexity of IC and microelectronics. The hardware attacks are classified into 2 parts, i.e., active attacks such as fault injection(results in IC malfunction and catastrophic system failures) and passive attacks such as side channel analysis (results in secret information leak, example – secret key of a cipher).Apart from faulty design or hardware, these attacks also result from the limited capability of the device.
1. As per the Bloomberg report[9], researchers found a tiny microchip embedded in a server’s motherboards. Though not part of the original design, they had been inserted at the factories during the manufacturing process. These chips allowed the attackers to create a stealth doorway into any network using these altered machines. This has affected almost 30 US companies, including Amazon and Apple Inc. These attacks come in the category of persistent malware.
2. Spectre & Meltdown: This attack exploits speculative execution, which is [10] an optimisation technique to improve CPU performance by guessing and performing in advance a series of tasks before being prompted to do so. The objective is to reduce the total execution time by keeping the information ready as it may be required at a later point. Spectre & Meltdown is about reading privileged memory with a side-channel or an indirect attack, using a program that monitors the subtle differences in timing required to access data by the CPU. This hardware vulnerability allows potential attackers to get access to data they should not have access to.
3. Other examples of hardware vulnerabilities include Bombe, Rowhammer attack, Thingbots, etc. Reference can be made of frequently encountered weakness in hardware design defined[11] at CWE (Common Weakness Enumeration), CVE (Common Vulnerabilities and Exposures) and NVD (National Vulnerability Database).
Firmware Attacks: With the adoption of 5G technologies and billions of devices getting connected, firmware attacks’ attack surface is becoming large. These attacks could be done remotely via Bluetooth, Wi-Fi, or any other kind of network connectivity.
1. ROCA[12] (CVE-2017-15361): This vulnerability was found in the implementation of RSA key pair generation used in cryptographic chips produced by Infineon Technologies AG. This vulnerability allowed a remote attacker to compute an RSA private key from the value of a public key. The private key can be misused for impersonation of a legitimate owner, decryption of sensitive messages and other related attacks.
2. MIRAI Botnet: This was one of the most significant botnet attacks. The most common attack originating from compromised devices is DDoS attack. Any network or service can get overwhelmed by huge number of targeted requests originating from botnet, a network of IoT devices under the control of a malicious entity. In 2016 a malware called Mirai infected computers and used them to search for vulnerable IoT devices like DVRs, cameras etc. These devices were, in turn, used to launch actual attacks against networks.
3. Intel Management Engine: The Intel® Management Engine[13] is an embedded microcontroller running a lightweight operating system that provides a variety of features and services for Intel® processor-based computer systems. There were instances where the attacker could gain physical access by manually updating the platform with a malicious firmware image through a flash programmer physically connected to the system.This could grant attackers remote Admin access to the system to execute arbitrary code with AMT execution privilege.
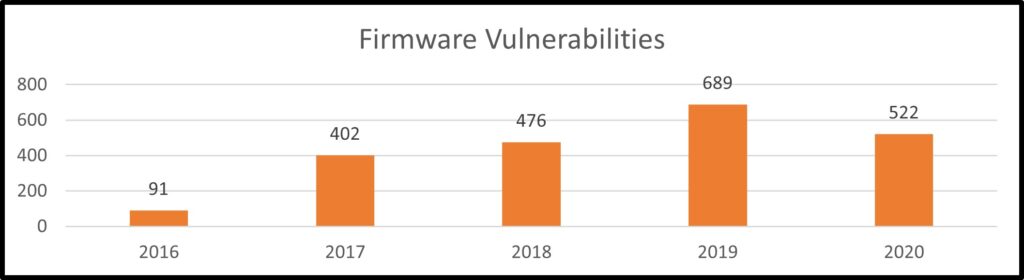
As per the last 5 years data of NVD[14], the firmware vulnerabilities grew by over 573%. These vulnerabilities allow attackers to compromise a device even before the system is booted up by pushing malicious software into the code on the lower levels, which regulates the hardware prior to and after system initialisation.
Cybersecurity Standards, Guidelines & Framework for Semiconductor industry
Standards: There are IT security standards (ISO/IEC 27001)as well as industry-specific standards that support the principle of security by design, address cybersecurity risks, and mitigate security vulnerabilities both at the hardware and software level. Example of industry-specific cybersecurity standards such as ISO/SAE DIS 21434 for road vehicles, ISA/IEC 62443 for industrial automation & control systems. We have observed the wide adoption of ISA/IEC62443 across other industries too, such as railways, medical devices, energy systems, IoT, etc. Some standards specific to IoT ecosystem include NIST 800-183, ITU-T IoT reference model, ISO/IEC CD 30141 reference model, and ETSI TS 103645 for consumer IoT.
Guidelines: The regulators and the industry/professional bodies often release guidance documents to manage cybersecurity risks. Example of it includes SAE J3101_202002 (hardware protected security for ground vehicles), SAE J3061A (cybersecurity guidebook for cyber-physical vehicle systems), AAMI TIR57: 2016 (Principles for Medical Device Security – Risk Management), and cybersecurity guidelines by FDA.
Framework: Along with these standards, there are cybersecurity frameworks such as NIST framework, which consists of best practices to manage risks. It focuses on 5 functions, i.e., identify, protect, detect, respond, and recover. It is based on international standards (such as NIST SP 800-x series, ISO/IEC 27001, ISA/IEC62443, CIS’s CSC – Critical Security Controls, COBIT framework by ISACA, etc.) and applies to any type of risk management and covers both preventive as well as reactive approaches.IoTSF (IoT Security Foundation) also defines holistic frameworks, which refers to industry-standard cybersecurity standards (e.g., UK Cyber Essentials, NIST Cyber Security, Framework, ISO27000 etc.)
Conclusion
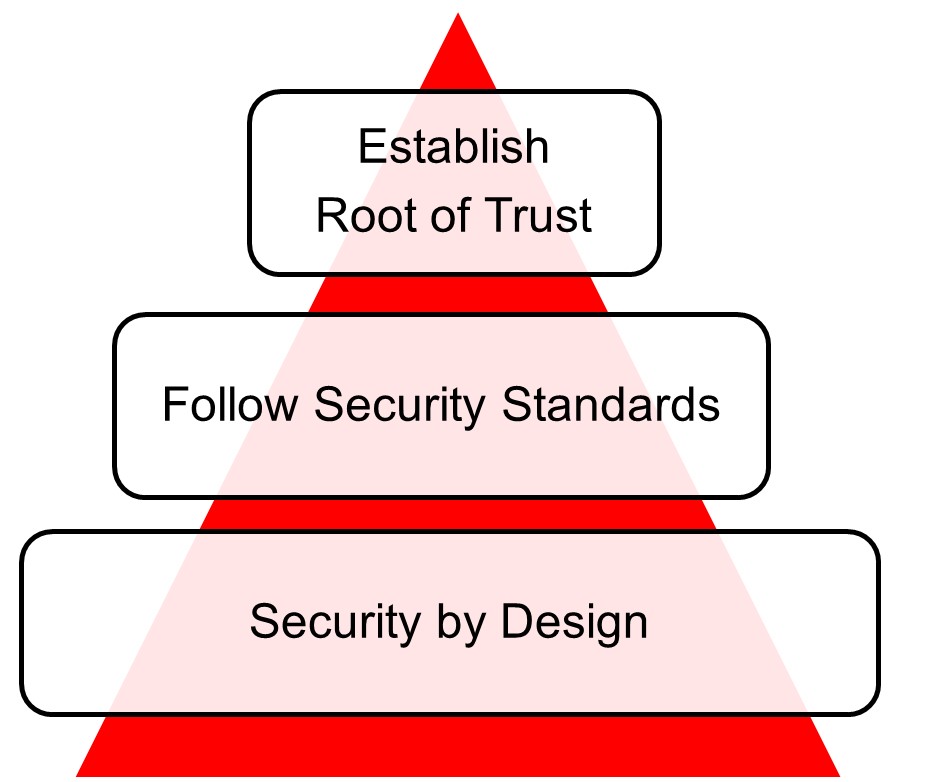
There is no single bullet to address overall security, and a single solution can not address 360-degree cybersecurity aspects. We need to start addressing the root of trust and create a standard driven certification ecosystem as successful cyber-attacks can destroy trust. Security is no longer an optional requirement; instead, it is a must. It must be architected into the system as it cannot be bolt-in later when the product is developed. We should use automated & qualified tools such as LDRA to identify and isolate cybersecurity vulnerabilities before the device is manufactured. It will help in saving costly design re-spins or catastrophic system failure due to a cyber-attack.
Authors:

Prashant Pandey is an engineering practitioner at STMicroelectronics with over 14 years of experience in designing IoT systems. He is a contributor at international standardisation organisations like Bluetooth® SIG. He serves as members of committees like BIS LITD17 Information Systems Security and Biometrics panel and India specific IoT standards committee under TEC (Telecom Engineering Centre), DoT. Prashant did his Bachelor of Technology from HBTU Kanpur and Master of Technology from BITS Pilani.

Himalya Bansal is a business development professional at LDRA. He is a CIG Member and Skills Development workgroup lead of Automotive CIG at IESA (India Electronics and Semiconductor Association). Apart from participation in international committees such as ISO/IEC JTC 1/SC 7/WG 26 (Software Testing) and ISO/TC204/WG18 (Cooperative Systems), he also contributes as a committee member in BIS (Bureau of Indian Standards) TED28 committee of Intelligent Transportation System and its P11 Panel on Cyber Security and Functional Safety of Road Vehicles. Himalya did his Bachelor of Engineering in Avionics from The Aeronautical Society of India and MBA in Marketing from Sikkim Manipal University.
References:
1. https://www.semiconductors.org/more-than-1-trillion-semiconductors-sold-annually-for-the-first-time-ever-in-2018/
2. https://www.globaldots.com/blog/41-6-billion-iot-devices-will-be-generating-79-4-zettabytes-of-data-in-2025
3. https://www.armis.com/bleedingbit/
4. https://www.dsiac.org/resources/articles/combating-counterfeit-components-in-the-dod-supply-chain
5. https://www.semiconductors.org/wp-content/uploads/2018/08/GSA_e-commerce_comments_july_2018.pdf
6. https://arxiv.org/abs/1907.08863
7. https://www.st.com/en/secure-mcus/stsafe-a110.html
8. Australian Government –IoTCodeofPractice – https://www.homeaffairs.gov.au/reports-and-pubs/files/code-of-practice.pdf
9. https://www.bloomberg.com/news/features/2018-10-04/the-big-hack-how-china-used-a-tiny-chip-to-infiltrate-america-s-top-companies
10. https://googleprojectzero.blogspot.com/2018/01/reading-privileged-memory-with-side.html
11. https://cwe.mitre.org/data/definitions/1194.html
12. https://crocs.fi.muni.cz/public/papers/rsa_ccs17
13. https://www.intel.in/content/www/in/en/support/articles/000008927/software/chipset-software.html
14. https://nvd.nist.gov/vuln/search/statistics?form_type=Advanced&results_type=statistics&query=firmware&search_type=all&pub_start_date=01%2F01%2F20xx&pub_end_date=12%2F31%2F20xx(where xx is year. such as xx = 19 if the year is 2019)






