We shop online. We work online. We play online. We live online. More and more, our lives depend on online, digital services. Almost everything can be done online – from shopping and banking to socialising– and all of this makes the internet, also known as cyberspace, an attractive target for criminals.
 What is Cyber Security?
What is Cyber Security?
Cyber security, also referred to as information technology security, focuses on protecting computers, networks, programs and data from unintended or unauthorized access, change or destruction.
The guiding principles behind information security are summed up in the acronym CIA
We want our information to:
1. Be read by the right people (Confidentiality).
2. Only be changed by authorized people (Integrity).
3. Be available to read and use whenever we want (Availability).
Malware
Malware is the collective name for software that has been designed to disrupt or damage data, software or hardware.
Depending on what the malware does, different terms are used to in relation to malware. For example:
• Ransomware is malware that demands payment in order to refrain from doing some harmful action or to undo the effects of the harmful action. More harmful malware like CryptoLocker literally encrypts your files and demands a payment before you can access them. Such types of malware are dangerous, especially if you don’t have backups.
• Spyware records the activities of the user, such as the passwords they type into the computer, and transmits this information to the person who wrote the malware
• Adware often comes along with spyware. It’s any type of software that displays advertising on your computer. Programs that display advertisements inside the program itself aren’t generally classified as malware. The kind of “adware” that’s particularly malicious is the kind that abuses its access to your system to display ads when it shouldn’t.
• Botnets are created using malware that allows an attacker to control a group of computers and use them to gather personal information or launch attacks against others, such as for sending spam emails or flooding a website with so many requests for content that the server cannot cope, called a denial-of-service attack.
The most common types of malware are:
Virus: A virus is a piece of software that has been written to insert copies of itself into applications and data and onto crucial parts of a computer’s hard disk. Viruses are said to be self-replicating programs. Viruses attach themselves to specific applications on a computer and are activated when the program is first run. At that point, the virus may make a copy of itself on the hard disk and continue to run, or it may only run each time the application is used.
Worms: Another type of self-replicating malware is the worm; like a virus it is designed to make copies of itself; but unlike a virus, a worm is a standalone application. Worms spread through network connections, accessing uninfected machines and then hijacking their resources to transmit yet more copies across the network.
Trojans: The Trojan is named after the wooden horse that supposedly smuggled Greek soldiers into the ancient city of Troy. A Trojan disguises itself as an entirely legitimate program (such as a screensaver), but behind the scenes it is causing damage – perhaps allowing someone else to gain control of the computer, copying personal information, deleting information, monitoring keystrokes, or using email software to pass itself on to other computers. Unlike viruses and worms, Trojans are not self-replicating; they rely on their apparent usefulness to spread between computers.
Passwords
Millions of people use online services every day, and it is crucial that these systems prevent users from accessing each other’s information. To do this, they need a way of uniquely identifying each user in a way that prevents users from impersonating each other. This is called identification and authentication.
Passwords and passcodes are the most common way of authenticating users. Examples of their use includes the PIN (Personal Identifier Number) you use with your debit and credit card as well as the many passwords you are expected to remember when logging in to computer-based services.
An ideal password must satisfy two conflicting aims. It should be:
1. memorable enough that the user can recall it without writing it down
2. Long enough and unique enough that no one else can guess it.
What happens when you enter a password?
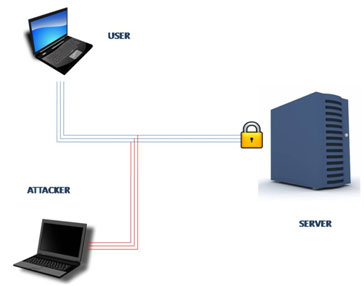
• When a user connects to the server for the first time, they may be asked to create a password so they can get access to the services.
• The user’s password is then sent over a network to a server database where it is stored.
• Whenever the user wants to access the services, they’re asked for the password.
• The filled password is sent over the network and compared to the stored password in the database. If the passwords match, the user is given access to the services.
• Any data sent over a network can be stored or intercepted so an attacker can easily store a password and log in as the original user.
• An attacker can also steal the database from the server. If this is to happen, data and passwords for all the users can be compromised.
To prevent data from being compromised while being transmitted as plaintext, we use a secure network link between the user’s computer and the server using strong cryptography. The most common form of encryption is the SSL Standard (Secure socket layer).
The other problem that we face is data being stored in the database as plaintext. To overcome this, we use a technique called hashing. A hash is the result of processing plaintext to create a unique, fixed-length identifier. It cannot be reconstructed even if the hash falls into the wrong hands. In this scheme, a hashing function is used to create a hash of a password, which is stored on the server – the password itself is discarded. When the user enters a password, their text is hashed using a copy of the same hashing function. The resulting hash is compared to the hash stored on the password server. Only if they match will the user be granted access. Almost all online services and computer systems store passwords as hashes – but surprisingly, errors still happen.
Attacking Passwords
The obvious ways that attackers can find or steal passwords, such as looking over your shoulder when you’re using an ATM or credit card machine or trying obvious passwords such as ‘abc123’ and ‘password’, are familiar to us.
One of the oldest methods of automatically breaking into computers is to perform a dictionary attack. As its name suggests, a computer will attempt to log into an account by working its way through one or more dictionaries – each entry in the dictionary is one possible password and if it doesn’t work, the computer moves on to the next. Dictionaries need not be the familiar A–Z references that we are familiar with: a concerted dictionary attack will also include more specialised reference works such as atlases, lists of astronomical bodies and characters from literature, as well as lists of the most commonly used passwords and lists of stolen passwords that are in widespread circulation.
Dictionary attacks can also be performed on the hashed values of words; they may take a little longer, but they will work. Some system administrators might set up dictionary attacks on their own users’ passwords to try to identify weak passwords that should be changed.
An alternative, simple attack is a brute force attack where a computer will methodically work through all possible passwords (so beginning with ‘A’, then ‘AA’, ‘AB’ and so on …) trying each in turn until it stumbles upon an actual password.
Dictionary and brute force attacks can be foiled by having computers watch for unsuccessful attempts to log in to accounts. Almost all computer systems restrict the number of unsuccessful log-ins after which the account is locked and can only be accessed after the intervention of an administrator.
Another type of attack on passwords is based on the incorrect configuration of the hashing technique used to store the passwords on the server.
Top 10 most common passwords
Here is a list of the most common passwords of 2014:
1. 123456
2. password
3. 12345
4. 12345678
5. qwerty
6. 123456789
7. 1234
8. baseball
9. dragon
10. football
How to pick a proper password
Using your pet’s name, your street name or a random word can be easy to remember, but can also be easy to guess. Even If the website uses hash functions, if the passwords are dictionary words, the attacker can generate lots of possible passwords, hash them and see whether any of them match a stored one. Attackers always start with dictionary words and variations thereof, as most passwords are normal words.
So your accounts will be more secure using passwords made up of a collection of numbers, letters and symbols that don’t resemble a dictionary word. Strong passwords – long, non-dictionary words that are not easily guessable – are vital. The other thing to remember is to use a different password for every account.
The majority of cases in which someone’s password has been compromised have occurred when an attacker has cracked someone’s password on a low-value, low-security site, and that user used the same password for another, higher-value site. The attacker either knows or guesses the target’s username on the higher-value site and then tries the cracked password on it.
Salt for protection
The security of stored passwords can be increased by a process known as salting – in which a random value (called the salt) is added to the plaintext password before the hashing process.
This greatly increases the number of possible hash values for the password and means that even if two people choose identical passwords, their hashed passwords have completely different values.
The hashed password and the relevant salt are stored by the password server. When the user attempts to log in to the computer, their password and the salt are added together, hashed and compared to the stored, hashed value.
Salting is only effective if:
• truly random salts are used for each password (some systems have either used a single salt for all passwords, or have only changed the salt when the computer is restarted)
• The salt is long enough that, when added to a password, it will create enough possible hashed values that an attacker cannot generate a table containing all possible hashes from a salted dictionary. A typical piece of advice is that the salt should be the same length as the output of the hashing function – so if your hashing function generates 256-bit hashes, a 256-bit salt should be used.
Open Authentication
For an increasing number of websites it is possible to use your existing online accounts, such as those provided by Google or Facebook, to register and log in. This approach for managing users’ account details depends on an authentication mechanism called OAuth (Open Authentication).
This method of checking a user’s identity requires the website to ask the user’s computer for some proof that the user’s identity has been authenticated by the OAuth provider (e.g., Google). This requires the user’s computer to first contact the OAuth provider where the user can input their username and password. The OAuth provider provides a digitally signed token that confirms the user’s identity.
So using OAuth can simplify your password management because all you need to remember is the username and password for your account with the OAuth provider. However, if you forget this password you will no longer have access to any of the accounts. Additionally, if an attacker gets access to this password, they will be able to access all the online systems you are able to access using your OAuth account details.
Two Factor Authentication
So, if a password isn’t secure enough, perhaps having two pieces of information is more secure? This is known as two-factor authentication and you’ve almost certainly used it without realising.
When you take money out of an ATM you have to give the bank two pieces of information – the first is the data stored on your bank card, the second is the PIN. Individually, neither can access your account, but when brought together they allow you to withdraw money.
Hardware security tokens
These devices contain a clock and a number generator which creates a new one-time password every minute or so. The bank synchronises the token with a master computer before issuing it to customers so the token and the master computer generate new passwords in time with one another. When the user is asked to enter the one-time password into their browser, they press a button on the token and enter the four or six digit number shown on the screen. The master computer will have also generated the same number. The two values are compared, if they match, the user is allowed into their account.
Two factor authentication on the web
A number of companies, including Apple, Google, Microsoft, etc support two factor authentication to improve the security for their web users. Rather than a single password, two-factor authentication requires the user to enter two pieces of information – their password and a changing value which is either sent by the website to their mobile phone, or generated by a companion application on the user’s own computer.
Cyber Security Breaches
• LinkedIn: In the middle of 2012, the hugely successful social networking site LinkedIn was attacked by Russian hackers. The passwords to some 6.5 million accounts were stolen, but although they were stored as hashed values, the passwords had not been salted. The hashing had been performed using the relatively old SHA-1 hashing algorithm which can be performed at very high speed. It was therefore not surprising that within a day, decrypted passwords were being published on the internet and LinkedIn was forced to ask all users to change their passwords.
• PlayStation Network: In April 2011, Sony revealed that the PlayStation Network, used by millions of consumers worldwide, had been breached by hackers. The breach went unnoticed by Sony for several days and ultimately resulted in the theft of up to 70 million customer records. The records included customer names, addresses, e-mails, dates of birth and account password details. In addition to the cost of fixing the breach, Sony was fined £250,000 by the Information Commissioner’s Office as a result of a ‘serious breach’ of the Data Protection Act. The precise financial cost to Sony is unclear but estimates place it at approximately £105 million, excluding the revenue loss by partner companies, damage to its reputation and potential damage to its customers.
• Adobe Systems: Over the years, Adobe had stored the names, addresses and credit card information of tens of millions of users on its servers. Then, in October 2013, Adobe admitted that data from 2.9 million accounts had been stolen. Later, that number was revised to 38 million accounts, but when the data file was found on the internet it contained no less than 153 million user accounts. Much of this data could be read and soon copies of the stolen accounts were in wide circulation. It also became clear that the people who had stolen user data had also gained access to Adobe’s development servers – program code, potentially worth billions of dollars, had also been stolen. Adobe was forced to change the log in details of every one of its users and to greatly improve its own security. And, of course, users are suing Adobe for not protecting their information.
• Target: In December 2013, the American retailer Target announced that hackers had stolen data belonging to 40 million customers. The attack had begun in late November and continued for several weeks before it was detected. By then it had compromised more than 110 million accounts, including unencrypted credit and debit card information as well as encrypted PIN data. By February 2014, American banks had replaced more than 17 million debit and credit cards at a cost of more than $172 million. The amount of fraud linked to the attack is unknown, as is the damage to Target’s reputation. Target was not the first major retailer to be hit by hackers, but this attack was different from most; the weakness that allowed the attackers into the Target computers lay outside of the company. The hackers had gained access through computers belonging to one of Target’s heating, ventilation and air conditioning services (HVAC) contractors. Like many large organisations, Target allows other companies to access its internal networks, to submit bills and exchange contracts. The hack appears to have begun when an employee of the HVAC Company received an email from one of their trusted partners. In fact, the email was fake and contained malicious software. Unlike traditional spam emails, this message had been targeted at a very specific audience – the HVAC Company. It was what is known as ’spear phishing’.
Once the email had been opened, the hidden software went to work and retrieved the HVAC Company’s Target network authorisations, allowing them to log on to their real objective. In an ideal system, the HVAC company’s authorisations should have restricted them to a network responsible solely for billing and contracts, but, like a lot of big organisations, Target used a single network for all of its data, allowing the attackers to eventually locate, and steal, customer data.







