Without an iota of doubt, safety and security of automobiles are two of the most critical areas of Automobile engineering today.
 Automotive Safety can be described as those measures for protecting the environment from the automotive. While measures for protecting the automobile from the external environment and intrusions can be classified as Automotive Security.
Automotive Safety can be described as those measures for protecting the environment from the automotive. While measures for protecting the automobile from the external environment and intrusions can be classified as Automotive Security.
Globally there are 50 million accidents and 1.2 million deaths every year. This simply means making a system safe is so very essential. Imagine a braking or a steering system not being reliable and predictable. Even a small variation of failure can be catastrophic to life and limb. With self-driving intelligent cars the magnitude of importance of automotive safety cannot be over emphasized.
Coming to security, the whole world has woken up to discover a fantasized science fiction come true – that of controlling an automobile remotely. Alarmingly it’s a lead to the unknown blackguards on the prowl. The hacking of the Jeep Cherokee by the now uber famous self-styled geeks Dr. Charlie Miller and Chris Valasek, has left Chrysler and other OEMs hankering for remedies to plug the holes in their cars. The geeks could do as much as take control of the Jeep remotely, switch off the engine and take over the maneuvering of the car! Expectedly the OEMS and Tier1s would get paranoid and renew their risk assessments and re-architect their safety and security systems.
In this article, we look at the trends in automotive electronics and attempt to look at what safety and security system risks arise out of them. We will then cover some Safety and Security methodologies and principles / tools that can remedy these risks. We will illustrate these with examples on how TI is helping electronics Tier1s design a safe and secure automobile of the future.
Automotive Evolution- Safety and Security Implications
Trends like Autonomous vehicles, Green Hybrid and Electric Vehicles with a major part of power train now electronics, Advanced Safety and Driver assistance systems managing the drive, Connected Cars, V2V, V2I and global Telematics with cloud managing the internetwork etc., the automobile is no longer a lone island.
Autonomous & ADAS features: such as self-driving vehicles, adaptive cruise control, lane departure control, collision avoidance, pedestrian detection, traffic sign recognition and speed control, all impacting actuation systems in the vehicle puts tremendous pressure on auto manufacturers to guarantee the safety and integrity of their ECUs or face the grave consequences thereof.
Electric/hybrid vehicles require special design considerations for safety for electric drivetrain components and batteries. For example, Tesla motors have had incidents of their cars catching fire originating from batteries. These have high voltages up to 600 volts requiring special insulations and such care. The OEMs need to take special safety precautions for conditions such as extreme temperatures, overcharging, short circuits, overheating etc concerning their electronic components and batteries.
Systems Consolidation: No system within the car is a lone island either. Each ECU is interconnected to others via various in vehicle buses and networks. Moreover each ECU is built upon over multiple MCUs/Processors each running independent and complex software but interacting with each other constantly. Furthermore we are seeing that multiple ECUs are getting merged and integrated sometimes being driven by a single SoC. This jeopardizes the critical portions of the system getting compromised due to vulnerabilities of the less critical and hence less secure components.
Software in today’s cars has increased manifold. Needless to say this has increased complexity due to the number of independent components, their interfaces and usage scenarios. Moreover some of the components are reused from open and publicly sourced freeware which is all too familiar to hackers for manipulation and reverse engineering. Cars today also provide connectivity & pairing with smart phones and storage devices which may be loaded with malware.
Connected Car and Telematics have created a whole new jigsaw exposing the cars to the cloud. Auto makers strive to differentiate by enabling features like remote unlocking, Remote diagnostics and assistance in case of a breakdown, Theft recovery, Automatic accident detection and response, advanced navigation features such as Real time traffic updates etc. typically via a cellular/satellite connection. If the cloud security or its channel gets breached, it risks the car security getting compromised. A lot of remote diagnostic services are not fool proof as they risk getting simulated by malware or malicious servers to gain access to the guts of the vehicle.
FOTA (Firmware Over The Air) is also a popular feature amongst both, customers and hackers.
The challenge is inescapable given that car manufacturers need to bite the bullet and provide newer and fancy features like some of the above – never ever whatsoever compromising on the safety and security of the automobile.
Designing for Automotive Safety
There have been numerous industry bodies and standards to ensure the safety requirements are met. Global standards like IEC61508 and ISO26262 are postulated by stakeholders in the industry. ISO26262 for instance is a functional safety management standard on safety life cycle for development and production of automotive products.
Further regulations like Euro NCAP, US NCAP, China and Bharat NCAP etc. are helping streamline the new car assessments by providing universally correlated rating systems.
Other software standards like AUTOSAR are developed by Auto OEMs and other stake holders like suppliers and tool developers for interoperability of electrical and electronics systems across ECUs and applications. This common API while it makes life easier for developers also make life easier for the hacking community – posing as a security threat which is not managed well.
TI Enabling Safety Architectures for Automotive Systems
An example of Safety support at TI are the TMS570 MCUs are open ARM CPU architecture based and have been steadily improving in performance, power and feature set. More than a Billion MCUs have been shipped into safety products for 20+ years into automotive and aerospace.
Built-in hardware diagnostics and certification to meet IEC61508 SIL-3 and ISO 26262 ASIL-D make TMS570 MCUs compelling.
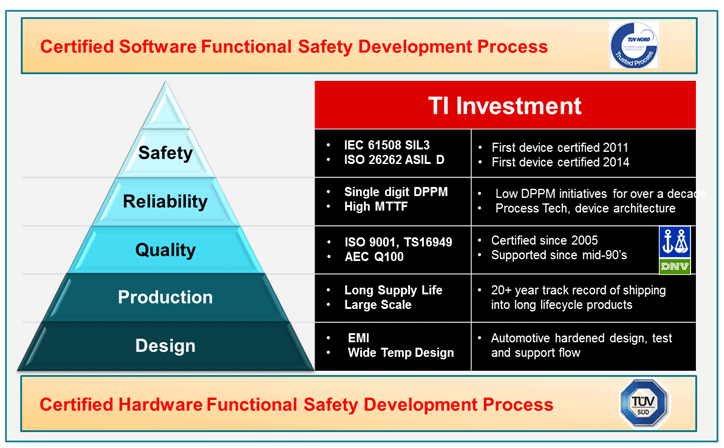 The SafeTI Software framework developed following ISO 26262 and IEC 61508 and is intended for product integration. There are safety documents, tools and software meant to decrease the development and certification time while the SafeTI Software Compliance Support Packages provide evidence to the safety standards.
The SafeTI Software framework developed following ISO 26262 and IEC 61508 and is intended for product integration. There are safety documents, tools and software meant to decrease the development and certification time while the SafeTI Software Compliance Support Packages provide evidence to the safety standards.
DSCs like C2000 with precise ADCs/DACs/PWM modules for applications like radar processing. They are also further used extensively to enable noise & EMC reduction with sinusoidal drive. Overall reliability made is possible by removal of rotor sensors.
Further numerous Analog and Power options qualified for automotive like PMICs, ADC/DACs, signal conditioners for sensors, Mixed Signal Analog, High performance FPDlink devices etc. help ensure safety of the overall system.
These offerings enable OEMs and Tier1s to build safe systems which are reliable and fail proof.
Designing For Automotive Security
Security implications and relevance today in a connected world has taken whole new dimensions. Risks like cloud connected car conceding personal info, financial data or even critical actuation control, to faceless remote agents was unheard of, a few years back.
Needless to say, there are several attempts by different consortiums to come up with frameworks for ensuring security. The EVITA project from EU defines three profiles (full, medium and light) of ECU implementation for Car2X and internal car network communications. Bosch has a HSM (Hardware Security Module) definition for automotive. HIS consortium (Audi, BMW, Porsche, VW, Daimler) has a specification called SHE (Secure Hardware Extension), IEEE 1609 (1609.2 for security) for V2X, etc.
KEY DESIGN PRINCIPLES AND CONSTRUCTS OF SECURITY
Secure boot – A hardware feature on ECUs that prevents booting from a tampered or modified firmware. Uses on-chip cryptographic key as a trust anchor and verifies if the boot firmware is from the trusted source i.e. OEM after confirming it is pristine.
Secure Island on the SoCs – A processor architecture that provides hardware isolation for secure software execution. An example is the ARM TrustZone® technology. For instance in an infotainment system there could be partitions for say cluster display subsystem which should be isolated from interferences of the lesser stringent multimedia sub system.
Protect everything critical using Encryption and Digital Signatures – All the more important given reverse engineering exposing the internal interworking of the ECUs and their intercommunication. Protection of the Cryptographic keys also needs to be taken care of. Keys that stored on-chip are more secure unlike keys on the external storages like Flash – which can be reverse engineered and exploited.
Tamper protection and resistance features upon opening up the box can kill the system and render unreadable to plug reverse engineering
Additional security features are being incorporated into the SoCs like the Crypto accelerator – the dedicated hardware processing block to speed up cryptographic functions at low power, the Secure counter – A non-volatile counter that only counts up and cannot be reset, the Secure clock – A tamper resistant clock modifiable in secure environment only, True random number generator – A hardware random number generator using some form of internal entropy source etc. are being utilized.
Hacks Explained and Possible Counter Measures
The Jeep Cherokee
The Jeep was hacked due to several vulnerabilities. The firmware code was read and reverse engineered as it was not encrypted. The boot firmware was tampered with and replaced. The FOTA firmware upgrade process loophole allowed disabling the integrity checks of the new firmware. CAN messages could be deciphered and exploited too. The debug/diagnostic modes of ECUs were fully exploited to put ECUs offline during active driving!
Furthermore the hackers exploited the vulnerability of the telecom operator which enabled them to remotely attack the infotainment system of cars from other cars and devices in the same network.
Security design considerations would have drastically reduced these vulnerabilities and prevented the hack. Along with proper care at all levels – the boot Firmware layers, OS kernel, IPC and application software – one could have ensured proper security precaution like Tamper protection and prevented the doctored boot in the first place. Encryption of the CAN messages would have made it a lot more tedious.
BMW Connected drive system
Here the hacker could reverse engineer the flash of the system and steal the key used to encrypt the SMS diagnostic/debug messages from the BMW services server and use them on all of the BMW model’s cars! The hacker exploited the vulnerability of the Cellular system by carrying a hacked Femto cell base station which could simulate the SMS messages to fool the connected drive system. By this he could issue commands to lock/unlock the car, etc.
A simple way to prevent this hack would have been to utilize a better secured key storage like perhaps a Secure on Chip keys. Furthermore a tamper protected system would have plugged the loophole way towards the beginning.
TI Enabling Security Architectures For Automotive Systems
TI supports secure features in its processors and even on some of the upcoming MCUs, for e.g. the TDAxx (TI Driver Assistance) SoCs and TI’s flagship Infotainment Jacinto SoCs cater to ADAS and IVI segments in the car. These SoCs have been equipped with ARM Core with Trust Zone and Virtualization extensions. Various features explained above and more are provided along with production support software for designing the state of the art security architectures for the connected world of the future.
Summary
There isn’t any doubt that only the paranoid and the proactive will survive in the industry. An automobile would be rated primarily based on how secure it is from intrusions and how safe it keeps those inside and outside it.
Texas Instruments has been partnering the Automotive electronic manufactures and OEMs shipping ICs for over 30+ years now. It is committed to continue providing innovative, fail safe and dependable automotive system ICs and associated software, tools and documentation to ensure the automobile is safe, secure and trustworthy.
About Authors








